No products in the cart.
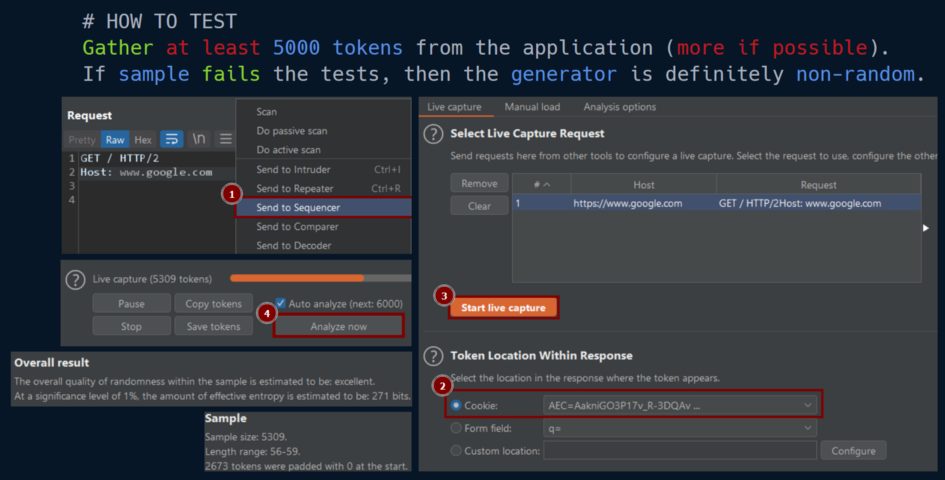
AppSec Tales VII | ACCESS by Karol Mazurek Application Security Testing of the Broken Access Control guidelines. INTRODUCTION This is the seventh article in the AppSec series, which describes how to test the application for Broken Access Control vulnerabilities to ensure a secure authorization process. The advice in this article....
Author
Latest Articles
 OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow
OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security
OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng
OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers
OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers
Subscribe
Login
0 Comments
