No products in the cart.
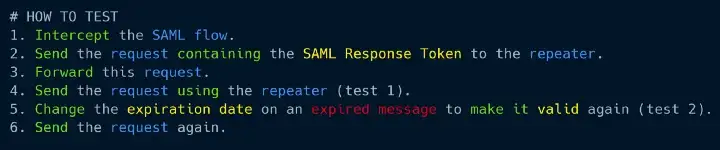
AppSec Tales X | SAML by Karol Mazurek Application Security Testing of the SAML protocol guidelines. INTRODUCTION The article describes the Application Security Testing of the SAML. The advice in this article is based on the following: OWASP Web Security Testing Guide OWASP Application Security Verification Standard NIST recommendations Bug....
Author
Latest Articles
 OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow
OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security
OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng
OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers
OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers

Many popular video games exist nowadays, but this one may be unfamiliar to you. Take some time to play it and experience its great qualities!