No products in the cart.
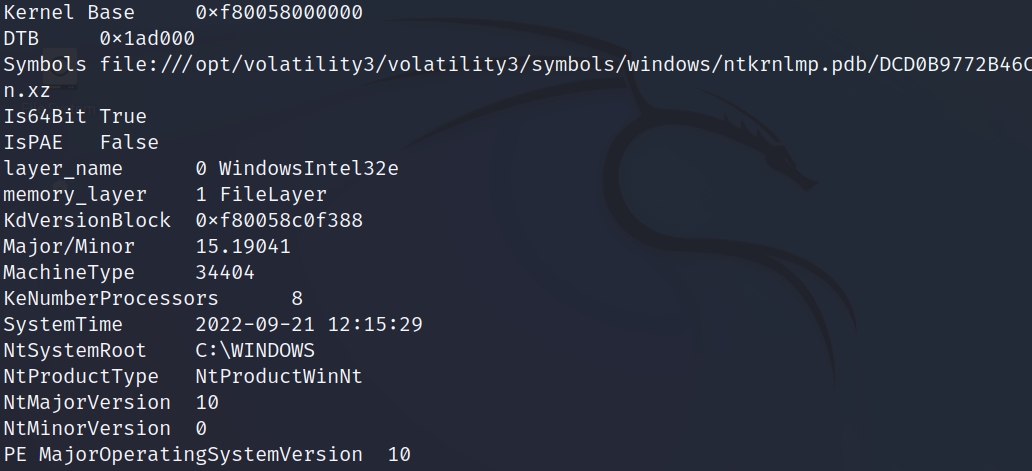
Bypass LSASS Dump protection with RAM Dump by João Paulo de Andrade Filho There is nothing more frustrating than an Antivirus blocking the execution of our tools and/or preventing certain actions to occur, like spawning a shell or blocking our attempts to dump the lsass process. Modern protections such as....
Author
Latest Articles
 OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow
OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security
OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng
OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers
OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers

The content of your essay appears to have piqued the interest of many people, and I must say that I am quite impressed with your post mapquest driving directions
This is something I’ve discussed with a friend. Run 3 is an addicting infinite runner game set in a futuristic universe in which you control a self-falling ball on a 3D track, combining old and new gameplay elements. A fast-paced game with some bizarre high-tech elements.
Your comments on the forum are very reasonable, hope you add comments to the run 3 website for us to improve further, and thank you for your comments.