No products in the cart.

Dear Readers, today we present you great interview with Prathan Phongthiproek who is creator of The Mobile App Pentest Cheat Sheet- which include penetration testing guide, tools and tool's commands. He told us his thoughts about the mobile application security market. Enjoy reading! [PM]: Can you please tell us something about yourself?....
Author
Latest Articles
 BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password
BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password BlogDecember 28, 2017Networks, What do you mean by that?
BlogDecember 28, 2017Networks, What do you mean by that?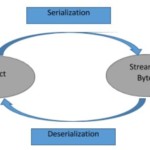 BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution
BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution BlogNovember 28, 2017Extending attack surface in distributed environments
BlogNovember 28, 2017Extending attack surface in distributed environments
Subscribe
Login
0 Comments
