No products in the cart.

"Are you such a dreamer to put the world to rights? I stay home forever where 2 and 2 always makes a 5" [Thom Yorke - 2 + 2 = 5] Acknowledgement I owe everything I know about x86 architecture to Xeno Kovah. A man who shared his class videos....
Author
Latest Articles
 BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password
BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password BlogDecember 28, 2017Networks, What do you mean by that?
BlogDecember 28, 2017Networks, What do you mean by that?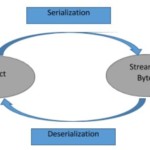 BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution
BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution BlogNovember 28, 2017Extending attack surface in distributed environments
BlogNovember 28, 2017Extending attack surface in distributed environments

Really informative and well explained, I enjoyed reading it all! Hope you’ll keep posting and perhaps add some images of Debuggers in the future.