No products in the cart.

Dear readers, today we have another great interview to share with you. We spoke with Jared Atkinson creator of PowerForensics. He told us everything about his tool: from technical to management side. Enjoy reading! [PenTest Magazine] Jared can you please tell us something about yourself? [Jared Atkinson] I am the Hunt Capability....
Author
Latest Articles
 BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password
BlogJanuary 26, 2018Effects of Biometrics Co-Used with Password BlogDecember 28, 2017Networks, What do you mean by that?
BlogDecember 28, 2017Networks, What do you mean by that?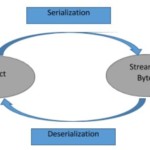 BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution
BlogDecember 4, 2017Thick Client Penetration Testing – Exploiting JAVA Deserialization Vulnerability for Remote Code Execution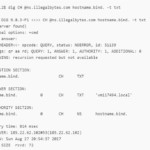 BlogNovember 28, 2017Extending attack surface in distributed environments
BlogNovember 28, 2017Extending attack surface in distributed environments
Subscribe
Login
0 Comments
