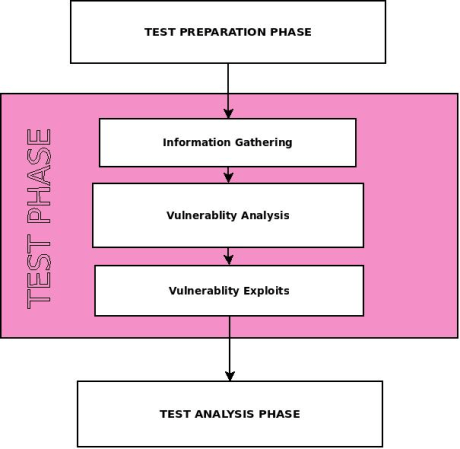
Penetration Testing using The "Kill Chain" Methodology is an online course in which you will learn how to perform Penetration Test step by step using the "Kill Chain" Methodology. This course is intended for technical astute audience and this is a 98% hands on course.
Course is self-paced so you can join any time!
The course is available only for premium subscribers.
18 CPE CREDITS
Information Gathering - Passive Reconnaissance
-
Netcraft.com
-
Whois Lookup
-
Linux Dig Command
-
Linux Traceroute and Mtr
-
Social Engineering ToolKit
-
And More ...
Sniffers - Passive sniffing
-
Wireshark
-
Etherape
-
Advanced MitM Framework
Vulnerability Analysis
-
OpenVas
-
Nikto
-
W3af
-
Exploit-db.com
Scanners Active scanning
-
Nmap and Zenmap
-
And More ...
Vulnerability Exploits
-
Veil-Evasion
-
The Metasploit Framework
-
And More ...
Test analysis
-
Client-side Exploitation
-
Exploiting targets with Armitage
Course structure:
-
four modules
-
course is online and self-paced
What you will learn in this course:
This course is intended for a technically astute audience.
The participant should have some general knowledge of the systems that we'll be testing. After covering some tools and techniques, you will have a good fundamental understanding of penetration testing and assessments.
What you will need (course requirements – software):
Pentesting OS:
-
Kali Linux - Free Download
Virtual Machine Applications:
-
VMWare Player - Free
-
VirtualBox - Free Download for Linux, Windows, and OSx
-
Parallels - Costs Money; For OS X
Other miscellaneous tools:
-
TeamViewer - Free; For remote live demos; Not required
-
Your Brain - Free
Virtual Machine Images:
LAMPSecurity Is designed to be a series of vulnerable virtual machine images along with complementary documentation designed to teach Linux, Apache, Php, Mysql security.
What skills you should have before you join:
-
We will use some of the most “popular” tools used in pentesting.
-
Some experience in IT Security, solid basic knowledge of TCP/IP networks.
-
Comfortable at the command line under Linux and Windows.
Your instructor:
Rupert Edwards
I’m a Linux professional possessing LPIC-3 Linux Professional Institute certification and CompTIA Cloud Essentials. I also have over 15 years of computer security experience, over 15 years of systems engineering as a security expert, 15 years as a lecturer and trainer, and 35 years of industry experience. Programming: PHP, Perl, Python, Ruby, Shell, and Penetration tester extraordinaire.
You can find me on G+ https://plus.google.com/u/0/+RupertEdwards
You can read an interview with our instructor here: https://pentestmag.com/the-kill-chain-methodology-interview-with-rupert-edwards/
PRE-COURSE MATERIALS - Free Download!
-> Pre-Course Material- Penetration Testing Using The “Kill Chain” Methodology
COURSE SYLLABUS
Module 1 – Information Gathering – Passive Reconnaissance
Topic 1: Netcraft.com
Topic 2: Linux commands
Topic 3: Social Engineering ToolKit
Exercise:
-
Use Linux commands to do passive Reconnaissance
-
Use Wireshark for passive sniffing the LAN
-
Use SET to set up fake clone website to steal user credentials.
-
Use SET to craft fake email and a malicious pdf document.
Module 2 – Vulnerability Analysis
Topic 1: OpenVas
Topic 2: Nikto
Topic 3: W3af
Topic 4: Exploitdb.com
Exercise:
-
Use tools learned in topic 1 thru 4 to perform a vulnerability assessment against LAMPSecurity.
-
Discuss vulnerabilities and remediation.
Module 3 – Scanners - Active scanning
Topic 1: Nmap
Topic 2: Zenmap
Topic 3: Advanced MitM Framework
Exercise:
-
Perform active scans against LAMPSecurity (target) in your pentesing lab environment.
-
Perform an man-in-the-middle attack against chosen target.
Module 4 – Vulnerability Exploits And Test Analysis
Topic 1: Veil-Evasion
Topic 2: The Metasploit Framework
Topic 3: And More ...
Exercise:
-
Craft malicious payload to bypass anti-virus.
-
Set up local web server to host the malicious payload.
-
Set up command and control server (C2 Server) with Metasploit Framework.
Test analysis:
-
Client side Exploitation
-
Exploiting targets with Armitage
Final Exam:
Good Luck ;)
Contact
Questions? Reach out to us at pt.courses@pentestmag.com.




Good Training
Although this course was few years old and there were some challenges in running few tools due to the version changes, but overall, conceptually and technically awesome course. Really boosted my confidence in doing a pentest. Thanks!!