
by Juan Morales
Free Internet!
Well, not really……The purpose of this article is to demonstrate different forms of Wi-Fi network attacks (with permission of course!) using none other than the Aircrack Suite. We will cover a slew of different attacks and capabilities of the Aircrack Suite. For the purposes of demonstration, I will be using an Alfa AWUS036ACH Wi-Fi USB adaptor though you can use any compatible wireless network adaptor that supports monitor and AP modes as well as packet injection. Without further ado, let’s go ahead and demonstrate how we can test different Wi-Fi standards.
Pre-Connection
Before capturing WPA handshakes for the purpose of cracking the password, we are going to go over two attacks (packet sniffing and deauthentication). Within the Aircrack Suite there is a tool named Airodump-ng. Airodump-ng serves as a packet sniffer, it also helps in attaining information regarding the networks in our vicinity and can even tell us information about the clients connected to those networks. In order to start using Airodump, we must first set our Wi-Fi adaptor to monitor mode. Monitor mode simply enables the Wi-Fi adaptor to receive different types of Wi-Fi packets, including “Beacon Packets”, which are sent by APs (Access Points) at regular intervals, “Deauthentication Packets”, which essentially reset a client’s network connection, and much more. The ability to receive the host of different packets is what allows Airodump not only to display different APs in the vicinity but also....
Author
Latest Articles
 OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow
OfficialFebruary 22, 2023Windows Privilege Escalation: The Concepts of Hijacking Execution Flow OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security
OfficialFebruary 22, 2023Building Intuition into Monitoring for OT/ICS Security OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng
OfficialFebruary 22, 2023WiFi Pentesting with Airodump-ng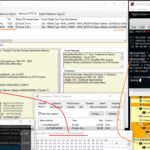 OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers
OfficialFebruary 21, 2023ETW vs Sysmon Against C2 Servers

The game has evolved into multiple expansions, such as Geometry Dash Lite, Geometry Dash World, and Geometry Dash SubZero, each adding fresh elements to the core experience. Many players initially discover Geometry Dash on their smartphones, ultimately transitioning to the PC version for improved control precision and access to extensive user-generated levels. Over time, geometry dash has secured a reputation for its steep difficulty curve, but it remains surprisingly easy for newcomers to pick up and enjoy thanks to simple tap-and-hold mechanics.
WiFi pentesting with Airodump-ng requires understanding wireless networks, packet capture, and analysis. It’s essential for used trimble tsc3 antenna identifying vulnerabilities and securing networks. Familiarity with command-line tools and interpreting data is crucial. This method empowers security professionals to assess and strengthen WiFi security effectively, enhancing overall network resilience.
thanks for the info
You seem to know what you’re dealing with, even though it’s hard to find knowledgeable people on this subject mapquest driving directions
This game is fantastic, and I used to enjoy playing it. doodle jump